In web development terms, hotlinking takes place when a remote server links to your images and uses them in their for their own purposes. Although it is a negative activity, the best way to deal with it is to not allow your content to be snatched. The easiest way to perform this task is to use Cpanel, Apache or .htaccess. The tutorial will describes these procedures with Cpanel and .htaccess.
Cpanel
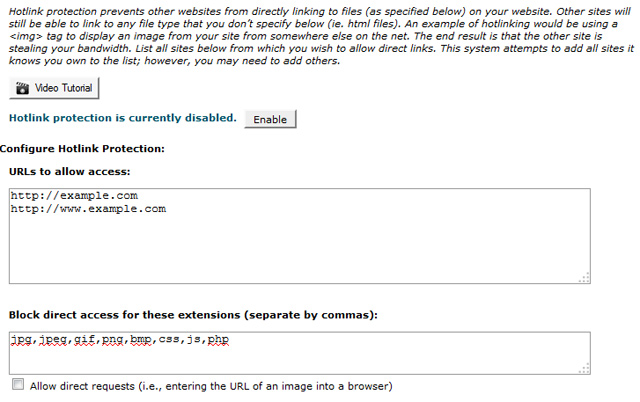
With Cpanel, you can login and select ‘Hotlink Protection’. Once you read this page, you can add your domains, file extensions and enable this feature. When you enable this feature, your .htaccess has these new directives written it. Although this feature convenient, it can leave a lot of code within the htaccess file, especially if you have many addon domains within a Cpanel account.
Alter Settings
HTACCESS
Using your HTACCESS file is a very good method to fine disable hotlinking. Adding the snippet below into your .htaccess file will result in example.com and example.ca domains to have access to the image links.
HTTP
HTTPS
The example below will disable hotlinking for http and https image links. The change from above is that it checks to see if the https variable is set. In the second set of conditions, the code allows only the https version of the website to pull images.
RewriteCond %{HTTPS} =on
RewriteCond %{HTTP_REFERER} !^https://example.ca/.*$ [NC]
RewriteCond %{HTTP_REFERER} !^https://example.ca$ [NC]
RewriteRule .*\.(jpe?g|gif|bmp|png)$ – [F,NC]
When you add ‘RewriteCond’ and ‘RewriteRule’, they come in pairs with the conditions followed by the rules. You can have multiple sets of conditions and rules.
Checking and testing Hotlinking
You can test to see if your images can be hotlinked by going to the websites
http://altlab.com/hotlinkchecker.php or http://www.htaccesstools.com/test-hotlink-protection/
Its is important to make sure that no images are kept in the cache when you make a check.
Varnish users
If you use the Varnish cache, you will need to restart the service with the Linux command line or use the Varnish Admin to flush the Varnish cache, in addition to clearing the browser cache(if necessary). The Varnish admin command is shown below.
A simpler way to explain the details above is to make sure to flush every caching system. If you use only Varnish, flush it. If you use browser caching, flush it.
Extra HTACCESS Tips
Now that you have hotlinking working, you may want to make a few other minor adjustments to your image files and folders. One major detail you may want to add to make sure thaat nobody can see a list of files within a folder.
To deny users the ability to read a list of files within a directory you can add one of theb two code blocks shown below. Although both give the desired results for hiding images, the first option hides all files from being listed while the second block does not allow listing to take place.
© 2018 ALL Rights Reserved | Sitemap
Vancouver | North Vancouver | Burnaby | Richmond | Coquitlam | Port Coquitlam | Surrey | Langley | Maple Ridge | Mission | Abbotsford | Kamloops | Kelowna | Victoria | Squamish | Whistler | Pemberton